Project Secrets
This section lets you manage data that you can share with one or more tool orchestration components that may require account credentials, keys, or other types of sensitive data.
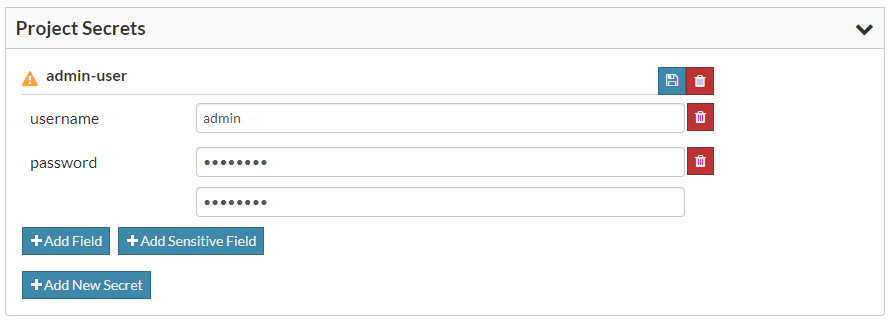
Click Add New Secret to start generating data for your secret, specify a name, and click OK to define your list of fields. To add a field, click Add Field. To add a sensitive field, click Add Sensitive Field. Specify a name for the field, and click OK. With sensitive data entry, your value is masked as you type, and you must confirm the correct value by entering it twice. Also, sensitive values are write-only and cannot be retrieved from the API of the Tool Orchestration Service. When you have finished specifying fields and field values, click the save icon button to store your secret.
Project secrets get stored as Kubernetes Secrets, so it's recommended that you follow the Kubernetes guidance on encrypting secret data at rest (https://kubernetes.io/docs/tasks/administer-cluster/encrypt-data/).
You can edit field values at any time, and you can undo an edit that's in progress by clicking the undo icon to the right of the field value. Project secrets support limited editing; you cannot change a secret's name, add or remove fields, or change the data entry mode for a field value. Click the trash can icon and Add New Secret to delete and recreate a secret that requires those edit types.
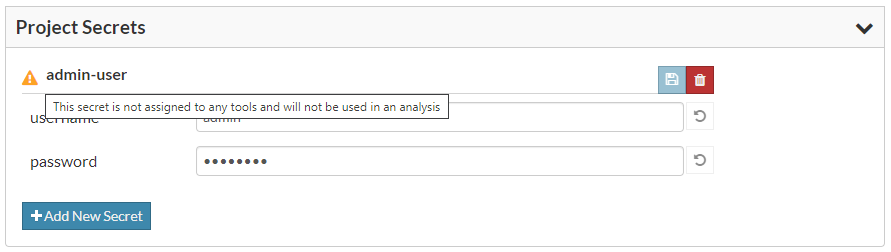
Project secrets are meant to be used with add-in tools, so Software Risk Manager will display a warning icon to highlight those that are not yet assigned to a tool. You can learn about assigning secrets to tools in the Customize Add-In Tools section.